Category: Authored Articles
How is Blockchain Revolutionizing The BFSI Sector ?
How is Blockchain Revolutionizing the BFSI Sector ?

SHARE
Blockchain technology drives tremendous changes across the BFSI industry. The decentralized financial services have brought up huge improvements to the centralized banking system.
So, let’s have a look at some of the major use cases of the blockchain technology in the BFSI sector:
- Know Your Customer (KYC)
Banking and financial institutions are highly concerned about the increasing costs that they have to bear to comply with the KYC. It is a lot of time-consuming processes; and it has to be performed individually by all banks and money based institutions. Nowadays, the banks need to upload the customer KYC data into a central repository to check the information of an existing or new customer.
With the help of a blockchain technology system, independent verification of each customer by one financial organization can be accessible for other organizations so that the one does not have to restart the KYC process again.
- Auditing and Bookkeeping
Standardizing the financial statement with the help of blockchain technology allows the auditors to verify the most crucial data easily and gradually. This decreases costs and even helps to save a lot of time. Blockchain technology makes it much more possible to prove the integrity of electronic files.
- Smart Contracts
The smart contract is a series of code, which runs when certain conditions written on it are completed.
With the help of smart contracts for banking, financial transactions help increase the speed of the complex processes. This also helps to make sure the accuracy of transferring the information as the transaction will be approved only if all the written conditions of the code are met.
- Digital Identity Verification
Identity verification is a significant part of each and every transaction that is made with your debit card or at your local bank branch. Your identity is indirectly linked to your assets.
- Fraud Reduction
The involvement of money in any circumstances increases the chances of fraudulent activities. Around 40% of the financial bodies are susceptible to heavy losses relating to economic crimes. The reason behind this can be the usage of a centralized database system for both the money and operations management. Blockchain is a secure, non-corruptible technology that works on a distributed database system. Therefore, there is no such chance of a single point of failure. All the transactions are stored in the form of a block with the help of a cryptographic mechanism that is very difficult to corrupt. Using blockchain technology can help to eliminate the cyber-crimes and attacks on the financial sector.
- Syndicated loans lending
There is one area of banking where the multiple institutions have come together to form consortiums to facilitate blockchain. Credit Suisse is one of those 20 big institutions, which are as of now working towards putting syndicated lending on the blockchain with the distributed ledger technology, more commonly known as the blockchain technology. As of now, this is an area that is still quite behind in terms of technology used. Fax communications, large delays in getting loans, and other hurdles are faced at the time of making and processing syndicate loans.
- Global payment options
Blockchain’s latest technology is internet-based and does not need any of the specific setups of operating users can access the data and conduct different transactions across the globe using their account public and private keys.
- Blockchain security
The first priority for any financial institution is in the area of security and privacy. And given the right and popular security patterns blockchain holds, most banks are obviously going to use this in storing assets that are of extreme value.
- Blockchain with AI
Banks do have a lot of tasks to process daily. And given that blockchain is now incorporated with Artificial Intelligence, most financial institutions will certainly want to use this because it will help in reducing their work stress and the rest. This will cover tasks like data storage, data monetization, and so on.
To Sum Up
This unique technology offers the banking industry with many unique opportunities, but certain challenges must be overcome for noticeable impacts to occur in the banking sector.
More so, the need for regulatory functions and oversight needs to be highly addressed by some of the relevant authorities. The financial sectors are synonymous with huge amounts of data. Moreover, data scalability must be sorted out prior to deploying blockchain in the financial sector.
In summary, blockchain can impact and revolutionize the banking financial sector. The only thing needed is its right application and feasibility.
SHARE
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Rapid Adoption of Blockchain Could Transform Emerging Economies into Financial Juggernauts – A Perspective
Rapid Adoption of Blockchain Could Transform Emerging Economies into Financial Juggernauts – A Perspective
Author - Vijay Kumar, Founder of DigitalFort Technologies

SHARE
A blockchain disruption is awaiting to unfold. While blockchain’s adoption would enforce transparency, security, regulatory compliance, robustness, non-repudiation, high availability, auditability & governance, its application would curtail Non-Performing Asset (NPA), impending frauds and political interference. Banking & Financial Services Industries (BFSI) would never be the same again with blockchain’s approach to inclusivity and quality, reducing operational overheads, commissions/fees while increasing profitability and earnings per share (EPS), eventually winning shareholders’ loyalties. In summary, blockchain could significantly add value through disintermediation; however, its adoption timeline could be longer.
Are Investment Banks Jittery About Blockchain?
Unlike any other industry, which gets affected by the recession, top US banks, except Lehman Brothers, have always remained amongst the top despite multiple recessions impacting everybody else. The reason is simple – banks have primarily made money in capital markets by being sole intermediaries – something no one else has a license to. For instance: the top 10 investment banks alone charge nearly USD100 billion in annual fee income (Indian data is not entirely available: Link).

Source: Financial Times League Table
Once Blockchain becomes mainstream, many revenues generating activities of investment banks will be performed by others – curtailing their hegemonies & steady revenue streams.
Blockchain Key Use Cases For BFSI

Source: Capgemini
Smaller firms & startups realize that funding through ICO (Initial Coin Offering) improves their profitability, given extra ordinary fees (7-10%) of these banks. Given its potential, blockchain will get adopted with time.

Could Blockchain Be the Next Gamechanger?
Most likely ‘a Yes’. Let us take a hypothetical example of a mid-size bank in an emerging economy (say Axis Bank in India). Axis Bank reported a basic EPS (earning per share) of INR 1.13 in FY 17-18. Had it implemented Blockchain for a mere KYC (Know Your Customers), it would have given its shareholders an EPS ranging from INR 5.82 to INR 20.95 (415% to 1754% return) despite a spike in its NPA – this could have made it a favorite at Dalal Street (India’s Wall Street).
KYC on Blockchain (Axis Bank Case Study – hypothetical illustration)
Axis Bank acquired Freecharge in 2017. The acquisition brought 5.4 crore Freecharge customers to the existing 2 crore customer base. Assuming 50% of Freecharge customers (i.e. 2.7 crores) & Axis Bank customers (i.e. 1 crore) needed KYC, Axis Bank must have had to do KYC for total of 3.7 crore customers. Let us examine the cost-benefit analysis of doing KYC on Blockchain. Average KYC cost (without Aadhar) to the bank is INR 1000 (Source) while KYC cost on Blockchain is less than US$ 5 (Source) & as per RBI (Central Bank), KYC is mandatory every 2 years for highly risky/leveraged customers in current economic/job scenario.
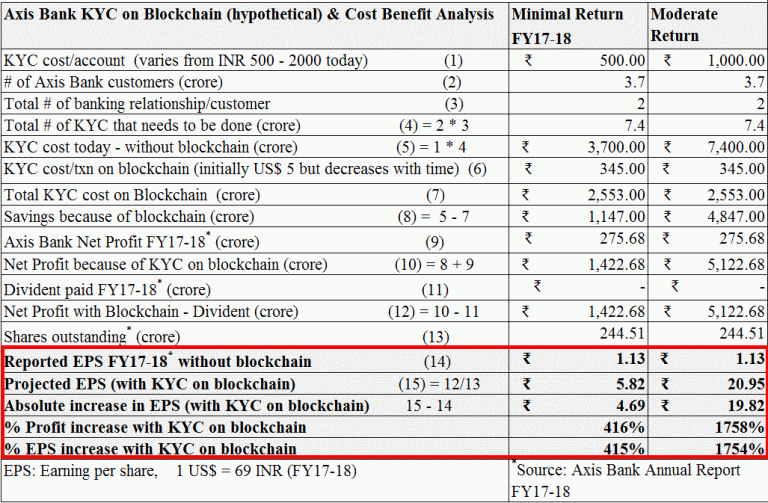
The questions are: if you were an Axis Bank shareholder, would you not be convinced that the bank needed to press ‘KYC on Blockchain’ competitive lever to attain such cost arbitrage amidst its rising NPA concerns? Second: if you were an entrepreneur, wouldn’t you once consider ‘KYC on blockchain as a Service’ potentially enticing? Most importantly, if 15 such Indian banks implement Blockchain, would it not easily create ample wealth to astronomically shoot GDP, disposable income, consumption levels and India’s growth rate?
The Puppets (PSU Banks CEOs) & The Genesis of India’s NPA
The onset of telephone banking in India began much before it did in the developed world & PSU Bank CEOs were mere puppets as the NPA game unfolded.
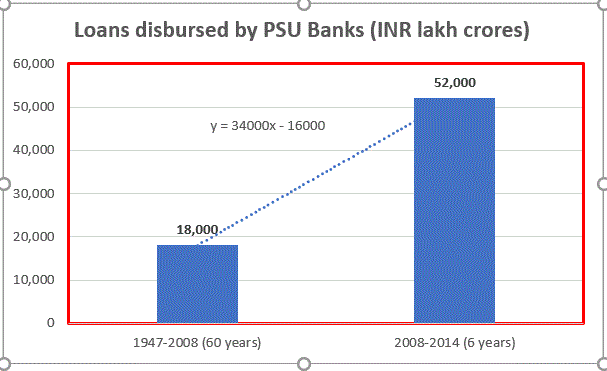
For the first 60 years post-independence (1947 to 2008), India’s public-sector (PSU) banks disbursed loans worth INR 18,000 lakh crores. Surprisingly, in just the next 6 years (2008 – 2014), they disbursed loans worth INR 52,000 lakh crores (almost 3 times of what had been sanctioned in 60 years was sanctioned in mere 6 years) – mostly at someone’s behest, mostly over mere phone calls (i.e. ‘telephone banking’) & mostly without much due diligence.
(Source: Honorable PM Mr. Narendra Modi’s speech rejecting No Confidence Motion against his Govt. at the Indian Parliament – July 20, 2018)
Why did this figure rise so astronomically in just 6 years?
Many of the initial loans had remained unpaid over the years & when time came to repay those loans, new loans were merely sanctioned just to close the earlier ones.

Source: The Economic Times
By budging to political pressures, these CEOs destroyed India’s financial prowess & their banks got grappled with daunting NPAs challenges. As most of these leaders are nearing their retirement age, they leave behind them legacies that they themselves would never be proud of.
Would Merging State-Run Banks (Vijaya Bank, Dena Bank & Bank of Baroda) Help?
This might not sound plausible. Both Dena Bank & Vijaya Bank don’t have a global presence – something Bank of Baroda complements with operations across 24 countries. However, would this merger curb the current NPA mess, the onslaught of potential Nirav Modis (i.e. frauds) and the never-ending political duress?
The question is: ‘Is there a way out?’
Can technology sturdily address these challenges while letting PSU banks CEOs craft legacies that they dearly would wish to?
Addressing NPA, Frauds, Inefficiencies & Political Interferences the Blockchain Way: Case Study — Punjab National Bank (PNB)
How Blockchain Could Have Averted India’s NPA, PNB Scam & Political Interference?
Once the blockchain smart contract is properly defined, it wouldn’t let anyone sanction loan to the defaulter, to customer with poor KYC/CIBIL score, or to customer who hasn’t undergone adequate due diligence, whatever be the political pressure.
- Letters of Understanding (LOU) details long with payment made against each LOU would have got propagated in real-time to all stakeholders (branch, head office & overseas associates).
- Given SWIFT messaging wasn’t integrated with the core banking system (CBS), smart contracts or hyperledger would have flagged this.
- Scamsters couldn’t have repeatedly tampered regulatory compliance records (e.g. KYC) and gone unnoticed.
- All transactions would have been transparent — something none would have been able to modify without consensus from others on PNB blockchain.
In summary, Blockchain could help combat fraud, NPA, inefficiencies & undue political duress.
Demystifying Blockchain

Source: bitsonblocks.net
A blockchain is analogous to a book. Each page, in a book, is like a block and is connected sequentially to the other by a number. Whenever a page gets tampered or torn, it gets easily identified. The same analogy holds, for blocks, in a Blockchain. Like legal contracts bring enforcement in the real world, Ethereum smart contract or hyperledger bring instantaneous facilitation, execution and enforcement of a negotiation/agreement in a blockchain.
Why Blockchain Suits BFSI?
Because of its inherent advantages (trustless/disintermediation, confidentiality, robustness, high availability & verifiability/auditability), blockchain has immense applications in BFSI.

Killer Applications
I. Trade Finance (Supply Chain)
90% of goods in global trade are carried by ocean shipping industry. As per Maersk, a shipment from East Africa to Europe goes through 200 different interactions/communications amongst network of shippers, freight forwarders, ocean carriers, ports and customs authorities. Blockchain has potential to vastly reduce the cost and complexity of trading by establishing transparency among parties and by reducing frauds, errors, transit times, inventory mis-management, wastage and cost while streamlining prompt vendor settlements.
II. International Fund Transfer (Payment)
Conventional overseas fund transfer is not helpful in a dire medical emergencies. If one wants to transfer funds overseas, he/she ends up paying substantial commission albeit the money reaches after 3 working days.

International Fund Transfer using Blockchain

SHARE
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Architecting Cyber Security
Architecting Cyber Security
Author - Vijay Kumar, Founder of DigitalFort

Corona Spiking Cyber Attacks?
After having decimated humans and animals internationally, the virulent corona has made inroads across the firewalls, the intrusion detection/prevention systems and the de-militarised zones(DMZ). Don’t get bogged down by these jargons, but the fact is hackers have been super active during the ongoing flu season. Cyber attacks have surprisingly spiked. Just recently, World Health Organization (WHO) was attacked (Source: Forbes) and such trends have increasingly been lately seen across many countries. In Italy alone, cyber attacks have increased by 200% during Corona regime.

Image: Corona & a specific cyber attack (Source: threatpost.com)
As per CSO Business Report,
- There is a hacker attack every 39 seconds.
- In 2018, hackers stole 0.5B personal records and over 75% of the healthcare industry was infected with malware in 2018-19.
- Most companies take nearly 6 months to detect a data breach.
- 95% of cybersecurity breaches are due to human error.
- Cybercrime damage costs would hit $6 trillion annually by 2021.
Security attacks dent not only an enterprise image but also it’s competitive positioning. As a result, enterprise security businesses are evolving like never before. Today there are more than 500 companies alone in cybersecurity space; there was hardly a handful a decade ago (Source).
No doubt, these firms help us become secure. However, implementing & continuously upgrading such solutions come at a cost. For an SME (Small & Medium Enterprise), this means an increase in the cost of operations and a dent in profitability. So, what should these firms do if they want to enhance security quotient in their application/product without having to spend too much on such solutions? The answer is obvious: build security in their offerings. But how? Let us delve onto one such idea – something not so commonly talked about.
Architecting Security: A Perspective on Software Dependencies
A software application relies on dependencies. A dependency arises at different times: it could arise either during system startup, application startup or during application execution/run time. Dependencies could be with libraries, third parties, registry keys (windows), configuration files (Unix), some expected inputs formats (from I/O operations or from user interfaces), required memory size, disk space usage or network availability.
Just imagine the scenario when one of these dependencies starts giving up – would your application still be reliable? Would it continue to behave the same way it is meant to be? And most importantly, how would you ensure that all dependencies that your application relies upon remain available, intact, robust & most importantly – “secure”?
At times & because of constraints (time, resource, cost, experience, etc.), these potential outcomes may not be considered during application design, leading to dreaded un-handled exceptions. Such dependency failures could take many forms: from application crashes to sensitive data (e.g. passwords) being dumped on to screen or on to some file. In the pursuit to identify such design flaws, attackers/hackers target such vulnerabilities & the exact time these dependencies get called. Once their research is done, they plan & execute such attacks.
So, what should we do to circumvent such malicious intent from these hackers
- Identify all your application dependencies. The more legacy the application, the more likely the vulnerability.
- Take a closer look at the time of usage of such dependencies.
- Now try to block usage of such dependencies (e.g. dll, api) as & when they get called.
- Now see how your application behaves in such deprived conditions.
- Most of the time, you would notice that application crashes or sensitive data (e.g. passwords) get dumped on to screen or onto some temporary file.
Let this be food for thought as you architect your next application. At the same time, could this be a lever for your Competitive Advantage? Absolutely, yes. Show how your competitor’s application crashes and how yours doesn’t? This could be a good enough reason to win the First Movers Advantage as you design your next software application.
Author: Vijay Kumar is the Founder of DigitalFort Technologies.
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Best Tools for Cloud Infrastructure Automation
Best Tools for Cloud Infrastructure Automation
The integration of Development and Operations brings up with a new perspective to software development. If you are new to the DevOps practices or looking to improve your current processes, then it can be a challenging task to know which tool is best for your team.
So, let’s take a look at the best DevOps Infrastructure Automation Tools, from automated build tools to application performance monitoring platforms.
- Ansible
Ansible automates a range of IT aspects, building configuration management, cloud provisioning, and application deployment. It is focused on the way various systems of your IT infrastructure interact with each other rather than managing a component at a time.
Ansible can be easily managed using a web interface called by the name as Ansible Tower. The tool offers a range of pricing models where users can choose from a basic, standard, or premium package and gets a custom quote for the features they use.
- Datadog
Datadog is primarily a monitoring tool for cloud applications. It offers detailed metrics for all your cloud applications, servers, and networks as well. It can be easily integrated with some other automation tools such as Chef, Puppet, Ansible, etc.
Datadog can help in quick detection and troubleshooting of problems within the system. Thus, it is quite a time and cost-efficient solution for managing your cloud infrastructure.
- Puppet
Puppet is an Infrastructure as a Code (IaaC) tool that lets users define the desired state of their infrastructure and automate the systems to achieve the same.
It monitors all your system and prevents any deviation from the defined state. Starting from simple workflow automation to infrastructure configuration and compliance, Puppet can do it all. The open-source tools are free, while the enterprise model for more than ten nodes is chargeable. Companies can get custom pricing quotes based on their requirements.
It is a tool preferred by companies such as Google and Dell; Puppet is the perfect tool to maintain consistency in the system while maximizing productivity.
- Selenium
Primarily created for testing web applications, Selenium is a robust tool for automating web browsers. It is the best tool in the market for web app testing and management. Companies can easily create quick bug fixing scripts as well as develop automated, regressive bug fixing mechanism with Selenium.
Selenium combines software, with each serving a different purpose: Selenium Integrated Development Environment (IDE), Selenium Remote Control (RC), Selenium WebDriver, and Selenium Grid. It is free, open-source software that can be sponsored under the standard Apache 2.0 license.
It is quite easy to use and install and offers support for extensions as well.
- Docker
Docker is a tool that focuses on continuous integration and deployment of code. Developers can easily create and manage applications using Dockerfiles.
DockerFIles enables application management in isolated environments, including system files, code, libraries, and other functions. Hence, it is highly preferred by companies engaged in multi-cloud and hybrid computing.
Docker helps to save up a lot of time and resources while enhancing the productivity of the system and can also be easily integrated with existing systems.
- Cisco Intelligent Automation for Cloud
Cisco provides with a number of cloud offerings, from private to public to hybrid solutions. Apart from these offerings, Cisco intelligent Automation for cloud gives everything from infrastructure as a service (IaaS) to hands-on provisioning and management of instances running in the Cisco cloud or in other cloud environments, including the VMware, OpenStack, and AWS.
Some of its excellent features include a self-service portal for users of your cloud, multi-tenancy and network service automation. Though created with Cisco’s own cloud infrastructure offerings in mind, Cisco Intelligent Automation for Cloud benefits from being able to extend the automation tooling into other ecosystems.
- Vagrant
Vagrant is an excellent tool for configuring virtual machines for a development environment. Vagrant runs on the top of the Virtual machines like VirtualBox, VMware, Hyper-V, etc. It uses a configuration file known as a VagrantFile, which contains all the configurations needed for the VM. Once a virtual machine is created, then it can be shared with other developers to have the same development environment. Vagrant has lots of plugins available for cloud provisioning, configuration management tools, and Docker.
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
7 Reasons you need workflow automation

7 Reasons you need workflow automation
Don’t you want to get the most out of your automating workflows software? If your workflow software is agile enough, then you can use it for far more than the typical HR and document management tasks that so companies use it for.
Automating workflows are not just about doing things faster and easier but also doing things better. Well, designed workflows can help to reduce errors and collect valuable data along the way – data that can be used for better budget planning, more effective customer tracking, and even faster recovery when disaster strikes. So, here are the 7 automating workflows use cases:
- Automatic Approval or Eligibility Evaluation
Do small purchase orders really need departmental approval? If not, your purchase order workflow can be made to automatically evaluate conditions to make sure that only purchases greater than a certain threshold amount be sent for the departmental approval. And should use try to game the system by submitting a series of just under the threshold purchases; the system can evaluate the number of purchase orders started by the same person with a defined time period and proceed accordingly.
- IT Support Tickets
Maybe your IT team consists of a single person hired to make sure that your computers and devices all work as intended. Even so, with the help of using workflow software to create an IT ticket system with online forms for users to describe their problems is smart. Not only are there no chances of losing requests, but your IT person can also collect valuable data and can help inform the future IT purchases or even make the business use case for hiring an additional IT worker.
- Submission of Tweets to Your Social Media Manager
If you have a social media team, it is often best to have a single person in charge of posting social media messages, Tweets, and the Like. A simple online form submitting Tweets to the social media managers makes sure that all of them meet specifications and that they are posted strategically at the time when they are likeliest to receive the attention they deserve. Such forms can also be valuable as should an old social media channel post need to be retrieved or taken down later on.
- A Disaster Recovery Workflow
Let’s suppose that your company experiences a natural disaster, break-in, or data breach. It is so much surprising and too difficult to know what to do first. But establishing a disaster recovery workflow can help. Such a workflow can walk users through essential steps, like bringing in extra staff, calling authorities, and contacting insurers. Too many businesses put disaster recovery on a back burner and are then caught out once something actually really happens.
- Managing Accounts Receivable
An automated workflow that flags AR items that are more than 30 days old can make sure that no accounts slip through the cracks and end up being written off. For example, when an account reaches the 30-days threshold, a reminder can be sent to an AR team member to contact the customer by email. When an account reaches a 60- or 90-days threshold, the workflow can prompt a team member to follow up by phone or certified mail in an attempt to collect all the money owed to you.
- Communication in distributed systems
Distributed systems become the new normal in Information Technology. Distributed Systems are complicated because of the eight fallacies of distributed computing. Most developers are not yet aware of the magnitude of changes coming due to the fact that remote communication is unreliable, that faults have to be accepted and that you exchange your transactional guarantees with eventual consistency.
Orchestration
Modern architectures are all about decomposition that is into server-less or microservices functions. When you have many small components doing one thing well, you are forced to connect the dots to implement the real use cases. This is where orchestration plays a big role. It basically allows the invoking components in a certain sequence.
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Use cases of Blockchain in cybersecurity

Use cases of Blockchain in cybersecurity
The collection of data and private information has been at a constant upward trend, and the value has crossed that of oil’s. These never fathomed a decade ago; events have resulted in cybersecurity threats being on the rise. In the year 2019 alone, governments, global enterprises, universities, and power companies have become victims of well-planned and elaborate hacks. It has become so much of an alarming concern that 75% of the CEOs of global giants plan on acquiring companies that handle cybersecurity or at least put that acquisition on priority.
Blockchain has the potential to be the latest technology that can aid in shielding businesses and some other entities against cyber-attacks. So, let us discuss the use cases where blockchain can help in this endeavor.
- Decentralized Storage Solutions
As we talked about in the beginning, data is becoming more valuable than oil, and it is not a surprise that businesses are accumulating customer data to make their marketing more effective. Anything that is so lucrative becomes a prime target for hackers. Since all the data is being stored in one place, all that a hacker needs to do is find a backdoor to that particular place. This makes all the information available for those with malicious intent to use them for anything that they would want to.
- Internet of Things Security
It is an unwritten rule among the hackers that the best way to gain access to the network or system is by exploiting the weakest points in the ecosystem. With the IoT kicking in, the number of devices like thermostats, doorbells, security cameras, and other household devices that are prone to cyber-attacks has considerably increased.
One of the key purposes of IoT is to transmit real-time data. With the blockchain securing the transmission and eliminating the need for a centralized authority to control the network, the transmission can happen without any lapses in the security from one corner of the world to another.
- Safer DNS
DNS is largely centralized. With this attribute, hackers can capitalize on the vulnerability to break into the connection between the IP address and website name to create havoc. This opens up a plethora of malicious possibilities – caching websites, redirecting users to spam platforms, or simply, which makes a webpage unavailable. A DNS attack can also be paired with the DDoS attacks to make a website or its utilities unusable for extended periods of time. While the tail log files can be used to issue real-time alerts for suspicious activities, the blockchain can take it a notch further.
- Security in Private Messaging
The first word in the phrase ‘private messaging’ holds a lot of importance. Conversational commerce is gaining lots of popularity, and a lot of metadata is being collected from the customers at the time of these exchanges. We have seen messengers like WhatsApp use end to end encryption. Some other messaging platforms are beginning to use blockchain to secure the information. Today, a lot of messaging applications are using a standard set of security protocols and a unified framework to enable cross messenger communication. Introducing a blockchain technology can tackle this issue and creates a new system of unified communication. Blockchain not only secures all data exchanges but also enables connectivity between the different messaging platforms.
Clavent hosts a free webinar on emerging technologies and practices every week and this week’s free webinar is on ‘Blockchain and cybersecurity’ on 04th April at 12 PM IST. Register yourself for free form here.
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
What is Design Thinking and Why is Everyone Talking About it?

What is Design Thinking and Why is Everyone Talking About it?
Design thinking originally came about as a way of teaching engineers how to approach problems as designers do. One of the first people to write about the design thinking was John E. Arnold, professor of mechanical engineering at Stanford University.
With the rise of human-centered design in the 80s and the formation of the design consultancy in IDEO in the 90s, design thinking became increasingly popular. By the start of the 21st century, design thinking was making its way into the world of business. In the year 2005, Stanford University, the school began teaching design thinking as an approach to social and technical innovation.
Design thinking is both an ideology and a process that seeks to solve complex problems in a user-centric way. It focuses on achieving practical results and solutions that are:
- Technically feasible: They can be developed into functional products or processes.
- Economically viable: The business can afford to implement them.
- Desirable for the user: They meet a real human need.
The ideology behind the design thinking states that, in order to come up with some innovative solutions, one must adopt a designer mindset and approach the problem from the user’s point of view. At the same time, design thinking is all about getting hands-on; the aim is to turn your ideas into tangible, testable products or processes as quickly as possible.
So,what exactly is design thinking?
Reasons why everyone is talking about Design Thinking:
- Design Thinking Focuses On the End-User
Design thinking is an approach that takes care of end-users at the center of the process to solve the problems. The main target is to develop useful products and solutions that will fulfill the needs of the user. The process is inherently human-centered, getting close enough to the user to see where their frustrations lie and how we can make their lives and experiences better and more fulfilling.
- Design Thinking Leverages Collective Expertise
By building multidisciplinary teams and having the discussion with many voices to the table, we come out of our respective fields or come out of the boxes to use our collective wisdom, expertise, and experience.
- Design Thinking Employs Empathy
The design thinking sometimes referred to as “understanding” or “discovery”, it is the foundation of the design thinking depending on the explanation, sympathy necessities that we look to comprehend and relate to the requirements and difficulties of the general population, the experience or the framework.
- Design Thinking Tests And Tests And Tests
The central process of Design Thinking is to “design, test and iterate”. It offers information about any kind of issues by creating several prototypes and taking actual users’ and customers’ feedback before spending too much time, effort or money, or anyone’s idea.
- Design Thinking Create Value at the time of Solving Real Problems
Design Thinking is all about creating value and solving problems, not just about creativity and innovation. Also, instead of going with the traditional ways, to solve problem Design Thinking seeks to use design principles for any industry.

Design Thinking Free Webinar
Date- 28 March 2020 | Time – 12 PM IST
Missed the webinar? We have the recording on YouTube so you can watch anytime you’d like.
RECENT POSTS
-
 Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR
Clavent’s Emerge 2020 Martech Summit Goes Virtual, powered by CleverTap08 Sep 2020 PR -
 Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR
Emerge 2020 HR Tech Summit Concluded Successfully12 Jul 2020 PR -
 Emerge 2020 HR Tech Summit12 Jul 2020 PR
Emerge 2020 HR Tech Summit12 Jul 2020 PR -
 My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles
My Experience Attending "How to Build High Performing Teams?" - Workshop On How to be a Good Manager.12 May 2020 Authored Articles -
 Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles
Top Quantum Computing Companies to look out for in 202029 Apr 2020 Listicles







